Table of contents
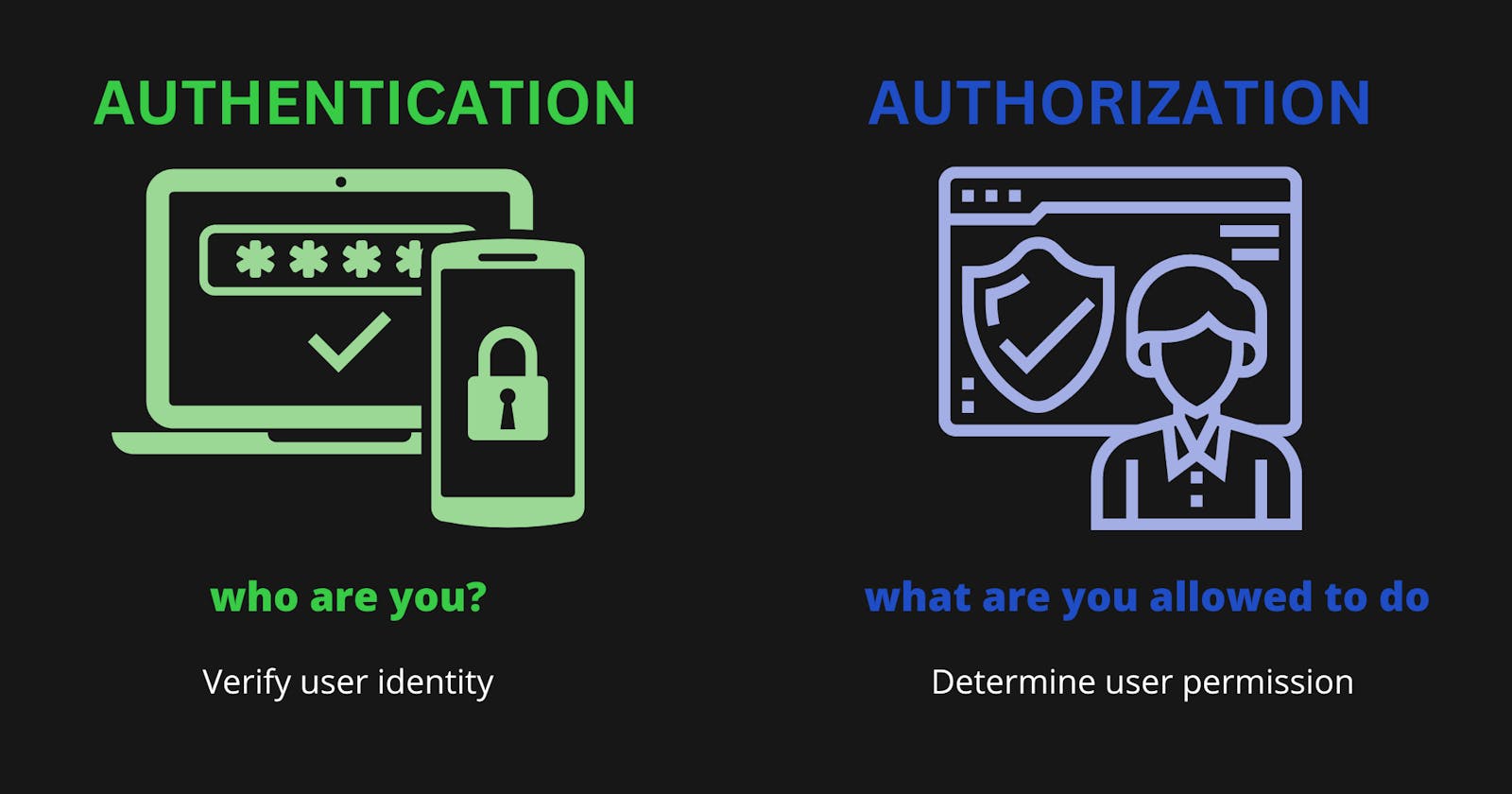
Authentication and authorization are two fundamental concepts in web application security that ensure that users can access only the resources they are authorized to access. In this article, we will explore the basics of authentication and authorization in JavaScript web applications.
Authentication
Authentication is the process of verifying the identity of a user. It is essential to ensure that only authorized users have access to protected resources in a web application. The most common way to authenticate a user is through the use of usernames and passwords.
When a user enters their username and password, the web application compares the credentials with those stored in a database or other storage mechanism. If the credentials match, the user is considered authenticated and granted access to the protected resources. If the credentials do not match, the user is denied access.
There are different approaches to implementing authentication in JavaScript web applications. Some common approaches include:
Basic authentication: In basic authentication, the user's credentials (username and password) are transmitted in the HTTP request headers using the
Authorizationheader. Basic authentication is not very secure, as the user's credentials are transmitted in clear text.Form-based authentication: In form-based authentication, the user's credentials are entered into a login form and submitted to the server. The server verifies the credentials and creates a session for the user.
Token-based authentication: In token-based authentication, the server generates a token that represents the user's session. The token is typically stored in a cookie or local storage on the client-side and included in subsequent requests to the server. The server verifies the token and grants access to protected resources if the token is valid.
An example of a token-based authentication
const express = require('express');
const jwt = require('jsonwebtoken');
const app = express();
// Define a secret key to sign the tokens
const secretKey = 'mySecretKey';
// Authenticate a user and return a JWT token
app.post('/login', (req, res) => {
const { username, password } = req.body;
// Validate the user's credentials
if (username === 'admin' && password === 'password') {
// Create a token with the user's ID and a secret key
const token = jwt.sign({ userId: 123 }, secretKey);
// Return the token to the client
res.json({ token });
} else {
res.status(401).json({ message: 'Invalid credentials' });
}
});
// Protect a route with token authentication
app.get('/protected', (req, res) => {
// Get the token from the Authorization header
const token = req.headers.authorization;
// Verify the token with the secret key
try {
const decoded = jwt.verify(token, secretKey);
// If the token is valid, grant access to the protected resource
res.json({ message: 'Welcome to the protected resource' });
} catch (error) {
res.status(401).json({ message: 'Unauthorized' });
}
});
// Start the server
app.listen(3000, () => {
console.log('Server listening on port 3000');
});
In this code above, the jsonwebtoken library is used to sign and verify JWT tokens. The POST /login route accepts a username and password, and if the credentials are valid, it returns a token containing the user's ID. The GET /protected route is protected by token authentication and can be accessed only if a valid token is provided in the Authorization header.
Authorization
Authorization is the process of determining whether a user has permission to access a particular resource. Authorization is a critical component of web application security as it ensures that only authorized users have access to protected resources.
There are different approaches to implementing authorization in JavaScript web applications. Some common approaches include:
Role-based access control (RBAC): In RBAC, users are assigned roles that define their permissions. When a user attempts to access a resource, the application checks the user's role to determine whether the user is authorized to access the resource.
// Define a middleware function to check the user's role function checkRole(role) { return (req, res, next) => { // Check if the user has the specified role if (req.user.role === role) { next(); // Grant access to the protected resource } else { res.status(403).json({ message: 'Forbidden' }); } }; } // Protect a route with RBAC app.get('/admin', checkRole('admin'), (req, res) => { res.json({ message: 'Welcome to the admin area' }); });The
checkRolemiddleware function in the code above checks whether the user has the specified role and grants access to the protected resource if the user has the role. TheGET /adminroute is protected by RBAC and can be accessed only if the user has the "admin" role.Attribute-based access control (ABAC): In ABAC, access control decisions are based on the attributes of the user, the resource, and the environment. For example, a user might be authorized to access a resource only if the user's department matches the resource's department.
// Define a middleware function to check the user's attributes function checkAttribute(attribute, value) { return (req, res, next) => { // Check if the user's attribute matches the specified value if (req.user[attribute] === value) { next(); // Grant access to the protected resource } else { res.status(403).json({ message: 'Forbidden' }); } }; } // Protect a route with ABAC app.get('/employees/:id', checkAttribute('department', 'IT'), (req, res) => { res.json({ message: `Details of employee ${req.params.id}` }); });In the code above, the
checkAttributemiddleware function checks whether the user's attribute matches the specified value and grants access to the protected resource if the attribute matches. TheGET /employees/:idroute is protected by ABAC and can be accessed only if the user's "department" attribute matches the value "IT".
Conclusion
Authentication and authorization are fundamental concepts in web application security. Implementing these concepts correctly is essential to ensure that users can access only the resources they are authorized to access. In JavaScript web applications, authentication is typically implemented using a username and password or token-based authentication, while authorization is typically implemented using role-based access control.